From CEO VIews Magazine: Entreprenuer Views
“To me, true thought leadership is seeing the practical ideas that others are not seeing.”
Jeff Richards, Managing Partner of CIO Professional Services, LLC
In today’s tech driven economy, building a close alignment between IT and business is a daunting task. That’s where CIO Professional Services, LLC steps in.
As a 15-year-old IT strategy consulting firm, CIO Professional Services helps mid-size organizations seamlessly integrate modern IT technology into business to address a wide range of IT alignment and strategy issues. As seasoned CIOs, they help you remove barriers and improve return on IT investment, while advancing your personal success.
At the helm is Jeff Richards, Managing Partner of CIO Professional Services, LLC. An inspirational leader with the ability to develop successful business strategies to cultivate tangible results, Jeff leads the Professional Services team.
In a recent interview with The CEO Views, Jeff Richards talked about his business story and how he is driving unparalleled success to business through effective thought leadership.
Kindly take us through your entrepreneurial journey! What inspired you to pursue a leadership role in this industry?
I actually started my career in manufacturing operations. Then I got more interested in putting in systems than running factories. I joined Ernst & Young, and worked my way up the ladder until I found myself managing 5,000 people across Europe, Middle East and Africa.
Soon I realized that although I was making lots of money, the job was eating my life, I wasn’t dealing with clients and learning new things, which is why I went into consulting, and I certainly wasn’t having fun. So, I moved back home from Europe, took off with a couple of other EY guys and opened up a little shop where I could start solving client’s problems and stay on the leading edge again.
You are widely regarded as an inspirational thought leader. Can you share any of your main intellectual breakthrough ideas or initiatives that you have pioneered?
Consulting is generally based on figuring out what’s wrong and then determining how to fix it. To address the first half of this – figuring out what is wrong – most consultants start their engagements by completing an assessment. One of our innovations was in creating a much faster and more efficient way to do this.
Back in the 1990s, most consultants completed their assessments by doing one-on-one interviews with a long list of people from the client’s team and then synthesizing the results of these serial interviews. It was a time-consuming and challenging process.
What we did was use some commercially available software that enabled us to pull everyone into a virtual room at the same time, where we led highly facilitated group sessions. All participants needed was a phone line and internet connection, which was very innovative at the time.
Not only was this a much more efficient process, we actually found that we got much more accurate assessments of the current situation. As we walked them through the questions, participants would often feed upon each other’s remarks when someone hit upon something.
These more accurate assessments, in turn, made it easier for us to ensure that our recommended solutions were all about the business. Because one of our guiding doctrines has always been that the business case must come first.






 By Sean Hickey, Senior Consultant
By Sean Hickey, Senior Consultant
 By Sean Hickey, Senior Consultant
By Sean Hickey, Senior Consultant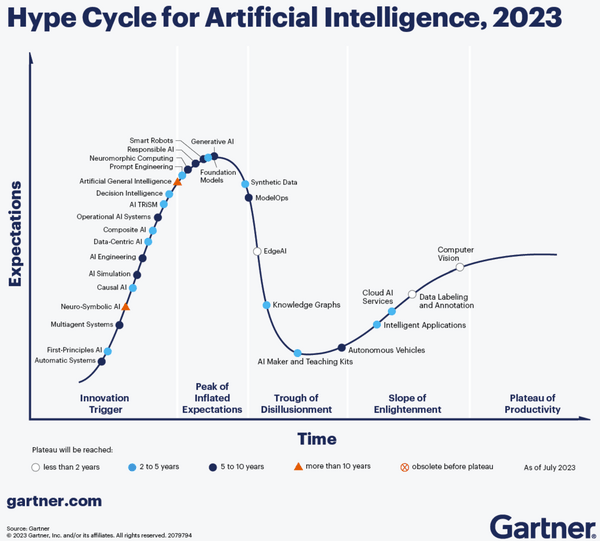
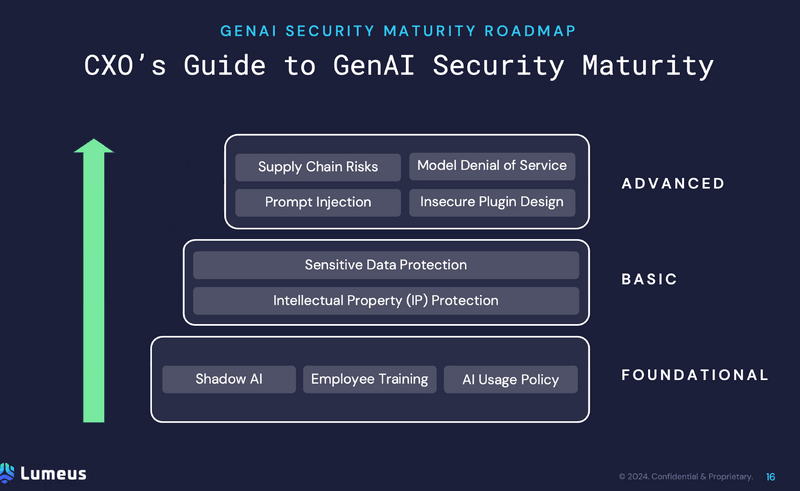
 By Ken Norland, Associate and Lonnie Sanders III, Associate
By Ken Norland, Associate and Lonnie Sanders III, Associate 
